

Damion Smy
2026 Suzuki Across PHEV is a rebadged Toyota RAV4 that Australia won't get
12 Hours Ago

Founder
When a new Toyota RAV4 belonging to a security expert was stolen recently without the key, he began reverse engineering the theft after the car was discovered, only to find the theft was initiated via the car’s headlights.
Cybersecurity researcher and automotive engineering consultant working for EDAG Engineering Group, Ian Tabor, said all the evidence pointed toward an effective execution of a CAN injection.
What exactly is a CAN? A controller area network (CAN) exists in most new cars on the road and it uses a set of devices that contain microprocessors to talk to other components within the car. This CAN then routes all the traffic around the corner to execute tasks – such as switching the headlights on.


So how exactly does one use the headlights to steal the car? According to The Register, a CAN injection allows a hacker to send a bogus message to the car’s CAN that makes it think the vehicle’s smart key is communicating with the car’s computer.
By entering via the CAN, would-be thieves are bypassing the wireless security measures in place that the key would otherwise first have to overcome before it can initiate commands through the CAN.
From this point, the vehicle accepts the request to unlock and then demobilise the car.
As we discovered in our recent video on theft of new cars, once a thief gains access to a new car like a Toyota RAV4, the process is then quite simple using tools on the internet to program a new key and delete the old keys.
Leading up to the theft of Tabor’s car, he noticed the headlight had been dislodged from his RAV4 and wiring had been exposed. He assumed that the car was damaged by another vehicle while it was parked. A few days later the car was stolen.
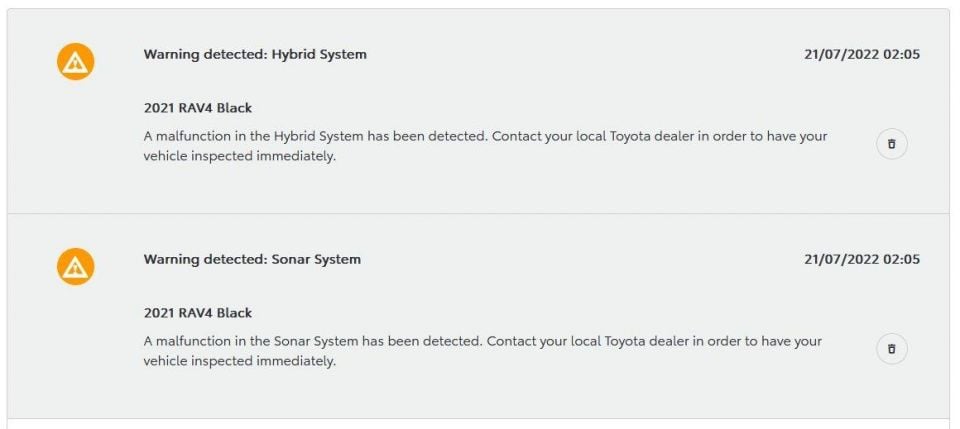
Tabor was able to reverse engineer the theft process by using his Toyota phone application to review logs of previous error messages. All the error messages pointed to electronic control unit (ECU) malfunctions that were driven by the thief attempting to hijack the vehicle.
Tabor hit the dark web to investigate how a hack like this could be performed. He discovered a device that looked liked a Bluetooth smart speaker that had cables tucked into the base of it. These cables could then be wired in to the vehicle’s exposed headlight cables.


Once connected, a button would be pressed on the faux Bluetooth speaker to initiate the CAN attack to then gain access to the vehicle.
Ken Tindell, CTO of Canis Automotive Labs detailed the attack in a technical report that goes into more detail about how it all occurred.
Moral of the story: it seems like no new car today is immune from theft.
Go deeper on the cars in our Showroom, compare your options, or see what a great deal looks like with help from our New Car Specialists.
Paul Maric is a CarExpert co-founder and YouTube host, combining engineering expertise with two decades in automotive journalism.


Damion Smy
12 Hours Ago


William Stopford
14 Hours Ago


Damion Smy
1 Day Ago


Max Davies
2 Days Ago


Damion Smy
3 Days Ago


William Stopford
3 Days Ago
Add CarExpert as a Preferred Source on Google so your search results prioritise writing by actual experts, not AI.